Monero (XMR) on Trezor Safe 5, Trezor Safe 3 and Trezor Model T
Monero (XMR) is an open-source cryptocurrency based on the CryptoNote protocol that focuses on privacy, fungibility and decentralization.
TABLE OF CONTENTS
- Overview
- Monero in Trezor
- How to use Monero with Trezor
- Exodus and Trezor
- Monero GUI
- Monero CLI
- Technology
- CryptoNote
- Ring signatures
- Stealth addresses
- Tail emission
- Kovri
- Bulletproofs
Monero is supported on the Trezor Safe 5, Trezor Safe 3, and Trezor Model T, and can be used with third-party wallets including Monero GUI and Monero CLI. Native support in Trezor Suite is currently not available.
Monero in Trezor
Trezor protocol is in line with the Monero cold-wallet signing protocol. Trezor implementation works with Bulletproofs. If the number of outputs is 2 (as for the vast majority of transactions), Trezor does all of the Bulletproofs calculations. For more than 2 outputs, the calculation is offloaded to a host (in the wallet) and then the Trezor device performs a check of the calculation. Using Trezor, there is no limit to the number of inputs/outputs, so these are the same as in Monero (16 for both).
How to use Monero with Trezor
First, make sure your Trezor Safe 5, Trezor Safe 3, or Trezor Model T is running the latest firmware.Monero with Exodus
Using your Trezor with Exodus allows for a seamless experience in handling Monero. The Exodus team has created a thorough guide to make this process even simpler, which can be found in their knowledge base. You can check it out here to learn more.
Monero GUI
- Download the latest Monero GUI from https://www.getmonero.org/downloads/
- Run monerod to sync your Monero blockchain
- Run monero-wallet-gui
- Choose 'Create a new wallet from hardware"
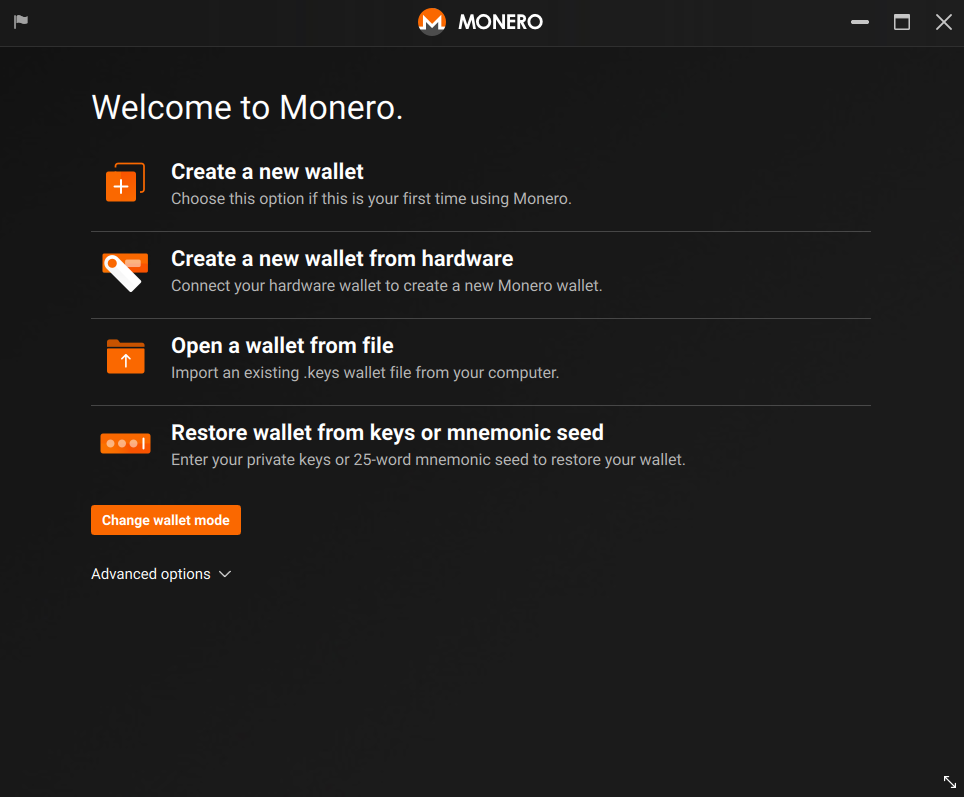
- If you have used your Trezor device with the Monero client before, choose "Restore a wallet from device. Use this if you used your hardware wallet before." (Use restore height 1692975). Otherwise, choose "Create a new wallet from device".
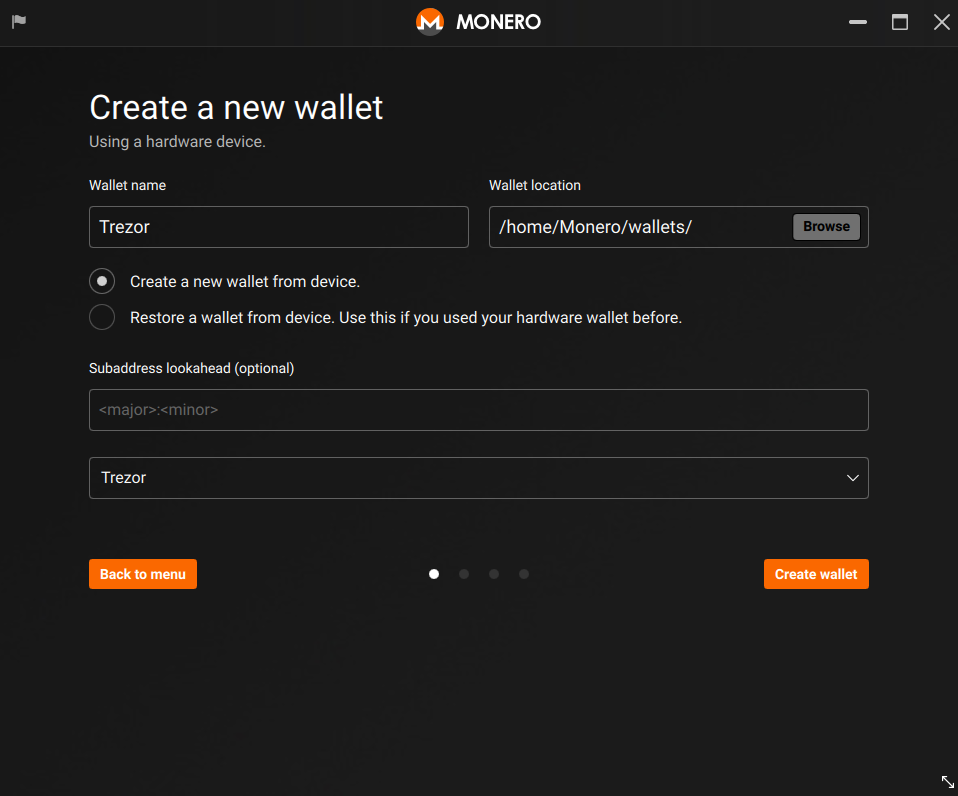
- If enabled, type in your passphrase and confirm exporting watch-only credentials on your device.
- You're then required to create a password to access your wallet. Please remember that this password cannot be recovered and you will be using it every time (during signing in or sending transactions) you use Monero GUI. In case you forget the password, you can recover your wallet using your Trezor device.
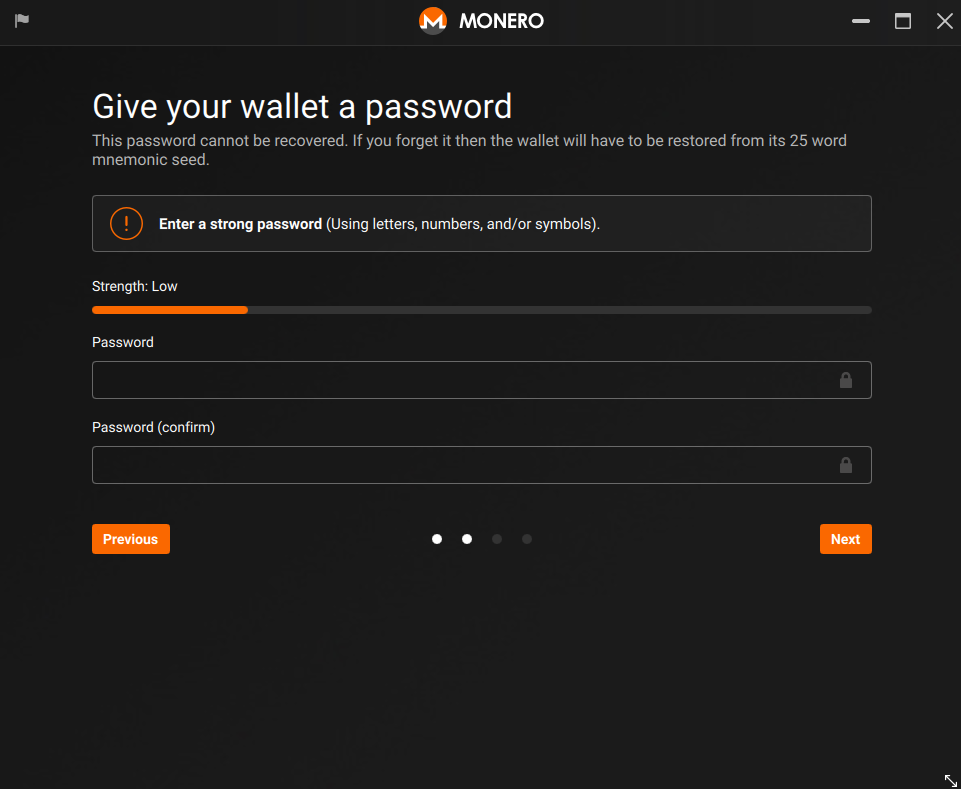
- If you're using your node, choose "Start a node automatically in background (recommended)". If you want to use a remote node choose "Connect to a remote node"
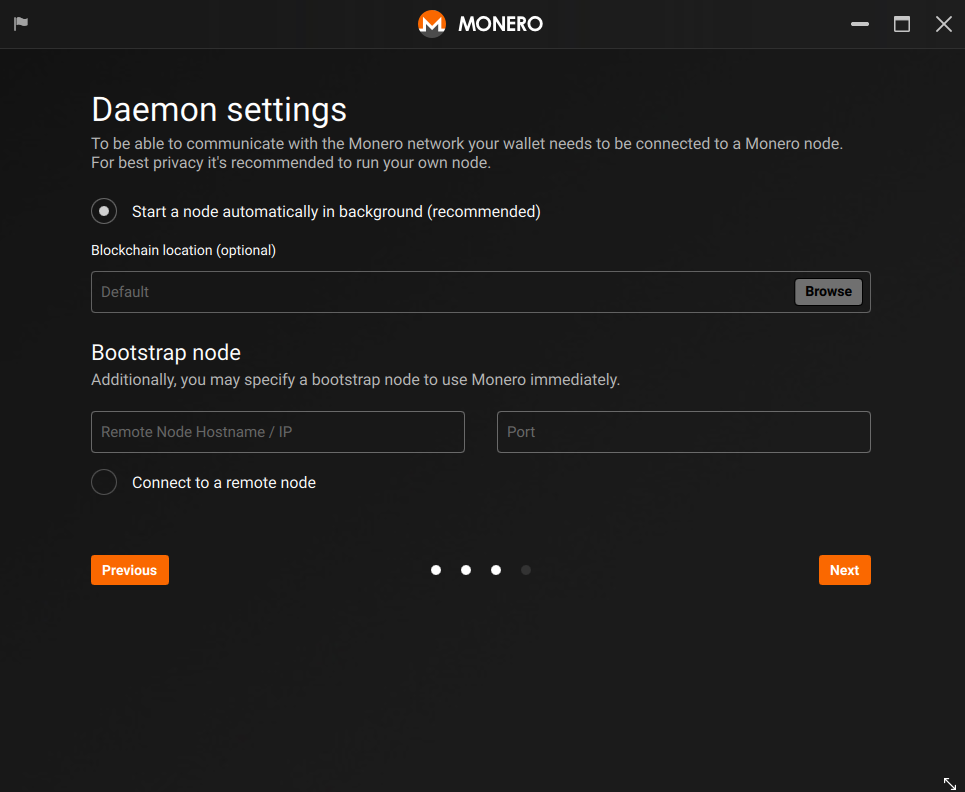
- You're all set up! You can now send your moneroj using Monero GUI wallet. Please check your Trezor device during the syncing, as you might be prompted to proceed with a refresh.
Monero CLI
- Download the latest Command-Line Tools Only release from https://www.getmonero.org/downloads/
- Synchronize the monero blockchain using following commands:
Windows:
Linux:
- Plug in your Trezor device, run Monero Wallet - Command line tools and generate your Trezor monero wallet:
Windows:
--restore-height 1692975
Linux:
--restore-height 1692975
- After creating your wallet, you can try to receive and send moneroj with Trezor device.
How do I generate a Trezor Monero wallet with the CLI (monero-wallet-cli)?
Monero wallet CLI guide
Technology
CryptoNote
The CryptoNote protocol was introduced by an unknown person or group of people under the name Nicolas van Saberhagen and published in 2013. It brought several improvements such as:
- blockchain obfuscation, confidential transactions
- self-adjusting variables (e.g., block size or fees)
- anonymous transactions and ring signatures
Monero is fork of Bytecoin which was the first cryptocurrency which implemented Cryptonote protocol.
Ring signatures
In cryptography, a ring signature is a type of digital signature that can be performed by any member of a group of users that each have keys. Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. One of the security properties of a ring signature is that it should be computationally infeasible to determine which of the group members' keys was used to produce the signature.
Since 10 January 2017, Monero uses Ring CT technology which not only hides the amount being sent, but also hides the funds from the public blockchain, only letting the recipient and the sender know how much was sent.
Stealth addresses
Stealth addresses are an important part of Monero inherent privacy. They allow and require the sender to create random one-time addresses for every transaction on behalf of the recipient. The recipient can publish just one address, yet have all of his/her incoming payments go to unique addresses on the blockchain, where they cannot be linked back to either the recipient's published address or any other addresses of the transaction. By using stealth addresses, only the sender and receiver can determine where a payment was sent.
Tail emission
Monero does not have a cap in total supply like Bitcoin, which means that Monero block rewards will never drop to zero. Block rewards will gradually drop until tail emission commences at the end of May 2022. At this point, rewards will be fixed at 0.6 XMR per block.
Kovri
Kovri is a C++ implementation of the I2P network. Kovri is currently in heavy, active development and not yet integrated with Monero.
Kovri will protect Monero users from:
- Node partitioning attacks
- Associations between a particular TXid and your IP address
- Mining or running a node in highly adversarial environments
- Metadata leakage (e.g., OpenAlias lookups)
Bulletproofs
Bulletproofs are a new non-interactive zero-knowledge proof protocol with very short proofs and without a trusted setup. The size of a bulletproof increases only logarithmically with both the size of the range and the number of outputs. This technology brought space savings, better verification times, and lower fees.