Dusting attacks & airdrop scam tokens
Trezor hardware wallets provide excellent security but do not eliminate all risks, such as falling victim to dusting attacks or airdrop scams.
A dusting attack involves receiving small amounts of cryptocurrency (dust) intended to track your transactions and potentially link your wallet to your identity.
An airdrop scam, on the other hand, typically involves receiving fake tokens that appear valuable, designed to trick you into interacting with them, which could compromise your wallet.
These attacks exploit user actions, such as sending or approving transactions involving the dust or scam tokens. It’s important to avoid interacting with unknown or unsolicited tokens and to stay informed about such tactics to protect your crypto assets.
How can I protect myself from dusting attacks and airdrop scams?
To keep yourself safe from the negative effects of dusting and airdrop scams, you can follow a few simple rules:
- If you receive any asset you were not expecting to receive, you should assume that it is a scam and not interact with it.
- When using Trezor Suite, do not engage with any of the tokens which are marked under the “Hidden” section unless you were expecting to receive those tokens
- On UTXO-based blockchains, keep good track of your UTXOs and make sure that you don’t accidentally consolidate dust UTXOs with the rest of your funds
- Regularly update your wallet software and learn about new types of blockchain scams to stay ahead of potential threats
Now, let’s dive deep into these two types of scams so you know how to identify them and keep yourself safe while on the blockchain.
What is dust?
The term “dusting attack” comes from the idea of dust, which is a term used to describe the tiny fractions of cryptocurrency that may remain after you have made a transaction.
Dust values are typically so small that they are (almost) entirely consumed by the transaction fee. This means tiny amounts of bitcoin or other cryptocurrency can get trapped in an address.
The minimum value at which your bitcoin (or other cryptocurrency) can be traded at is also called the dust limit.
Dust may be cleaned up by performing manual coin selection via coin control, which lets users select specific coins (UTXOs) to spend in a transaction.
For more information on this, please read our articles called What is a UTXO? and Coin control in Trezor Suite.
However, before you clean up your dust, make sure that you understand exactly what a dusting attack is to avoid impacting your on-chain privacy!
Dusting attacks
A dusting attack is a type of attack which happens on a blockchain. Attackers send small amounts of cryptocurrencies to many wallets simultaneously for various purposes depending on the type of cryptocurrency.
While it may seem harmless to receive small amounts of dust, there are several ways that attackers can use dust to either track you on-chain or to try and trick you in various ways to separate you from your hard-earned cryptocurrency.
Receiving dust transactions in your wallet is normal and not a cause for concern. While this is less common on Bitcoin today, it remains more frequent on other blockchains. Dust transactions pose no risk if handled correctly.
How do dusting attacks work on Bitcoin?
The first dusting attacks emerged on Bitcoin. Attackers exploited users' lack of understanding about UTXO (Unspent Transaction Output) management. They sent tiny amounts of Bitcoin, often just a few satoshis (the smallest unit of Bitcoin), to random wallet addresses.
If users consolidated these small amounts with the Bitcoin in their other addresses, attackers could trace the transactions and link addresses together, revealing wallet balances and ownership patterns. This made high-value wallets vulnerable to further targeting or scams.
As Bitcoin grew in popularity, the cost of transactions increased, making dusting attacks on Bitcoin less practical and less common.
Not all dust transactions are intended to track you. Sometimes, dust is used for purposes like advertising or spamming the network to manipulate transaction fees. If you receive a dust transaction on your Bitcoin wallet, simply avoid interacting with that specific UTXO. Don’t consolidate or spend it, and your on-chain privacy will remain safe!
It is interesting to note that there have been cases of blockchain investigators and exchanges using dusting to track stolen funds.
To learn more about dusting attacks on Bitcoin and their decreasing frequency in modern times, you can read this in-depth analysis by Bitcoin expert Jameson Lopp here.
What about dusting attacks on other blockchains?
Due to the Bitcoin network’s increasing traffic and fees, attackers shifted to cheaper UTXO-based blockchains like Dogecoin and Litecoin, where dusting attacks remain economical.
However, innovation among attackers didn’t stop there.
On non-UTXO blockchains like XLM and XRP, scammers began sending tiny transactions with embedded memos or messages containing links to phishing websites. These sites were designed to trick users into revealing wallet backups.
Do not visit any websites which appear in your wallet as a token, and under no circumstances write your wallet backup into any website! This is a common scam which will drain your entire wallet.
This expanded the scope of dusting attacks beyond privacy breaches to direct theft, and eventually led to the creation of the airdrop scam token.
Airdrop scam tokens & NFTs
Today, malicious smart contracts and NFTs dominate incidents on blockchains like Ethereum, Solana, and BNB Smart Chain. Attackers airdrop scam tokens or NFTs into wallets. If a user attempts to sell or transfer one of these assets, they inadvertently interact with a malicious smart contract that drains their entire wallet balance.
For example, scam NFTs often appear in wallets and are visible on marketplaces like OpenSea. When users engage with these assets the embedded smart contract executes a transaction which empties the wallet and sends the full balance to the scammer. Users can be tricked into thinking that they are, for example, claiming an NFT airdrop when in reality they are sending their funds to a scammer.
Since version 24.7.3 of Trezor Suite, scam airdrop tokens are blurred and sorted into their own "Hidden" section.
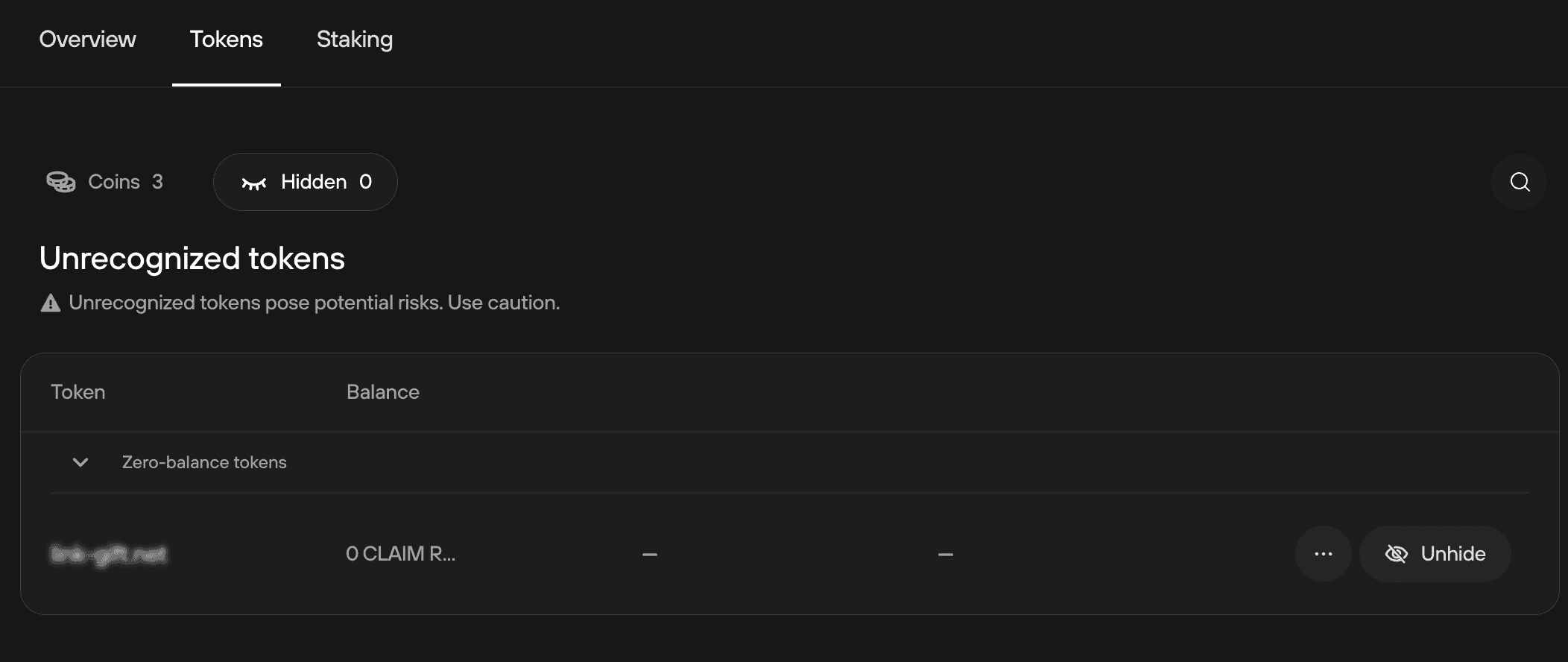
Do not engage with any unexpected airdrops or transactions on any blockchain. NFTs and tokens with messages in the transactions are especially risky to engage with — don’t do it!
Watch out specifically for token approval transactions. While these are often necessary to interact with specific tokens or trade them on decentralized exchanges like Uniswap, they can also grant malicious contracts unlimited access to your funds. Always review the transaction details carefully. Verify the spender address, limit the approval amount, and only interact with trusted platforms or contracts.
Oftentimes, a third-party wallet will even give a warning regarding what is about to happen, but it can be easily dismissed by users who are unaware of the possible consequences of a token approval transaction.
Some dust transactions may appear as high-value tokens, such as a large amount of fake tokens posing as USDT. These scams are designed to trick users into believing they’ve received a large sum of money by mistake. Interacting with these tokens can compromise your wallet and drain your funds.
Avoid engaging with unknown tokens, and always verify transactions carefully before taking any action.