What is a hardware wallet?
A hardware wallet is an electronic device that stores the to your cryptocurrency wallet. Hardware wallets never connect to the internet. A hardware wallet interfaces with your computer, allowing you to interact with the blockchain without exposing your private key to the internet.
Keeping your private key offline is essential for security. A Trezor hardware wallet enables safe transactions and real-time access to your assets, all while protecting your private key.
- Hardware wallet basics
- How do hardware wallets work?
- Why are hardware wallets essential for security?
- Types of wallets
- Key features to look for in a hardware wallet
- How to set up and use a hardware wallet
- Best practices for hardware wallet security
- How to choose the right hardware wallet for you
- Frequently Asked Questions (FAQs)
- Final thoughts – why every crypto holder should consider a hardware wallet
Your private key is the key to your cryptocurrency. Anyone with access to your private key can send funds from the addresses it controls!
Hardware wallet basics
A Trezor hardware wallet securely stores the private key to your cryptocurrency. When connected to your computer, it lets you access and manage your assets without exposing your private key to the internet.
In the early days of cryptocurrency, private keys were stored in encrypted files on people’s computers. Back then, it wasn’t unusual for someone to have their entire wallet drained by malware.
In 2014, SatoshiLabs was founded in Prague and created the Trezor Model One - the world’s first hardware wallet. We took private keys offline in a simple way and made Bitcoin and other cryptocurrencies more accessible to the rest of the world.
Since then, we’ve been hard at work innovating and building cryptocurrency’s future!
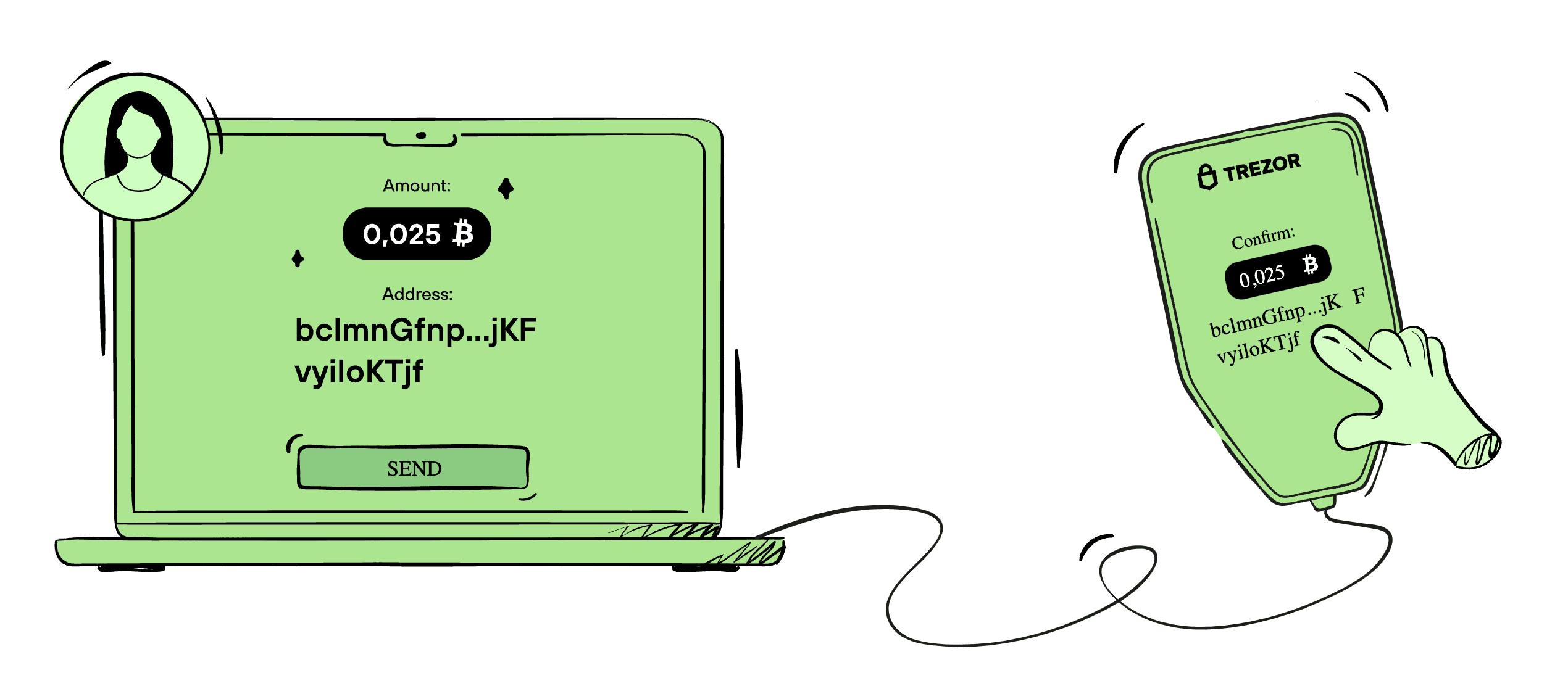
How do hardware wallets work?
Cryptographic keys are the basic principle that fuel cryptocurrency wallets. There are two types of keys you should know about - private keys and public keys.
A public key is like your bank account number. It’s safe to share and allows others to send cryptocurrency to you. A private key, however, is like the password to your bank account. It must be kept secure, as it grants access to your funds. Hardware wallets protect your private key by keeping it completely isolated from the internet, safeguarding it from hackers and malware.
When you make a wallet, your private key is encrypted through a one-way cryptographic algorithm which creates a public key. This means that you are not able to figure out a wallet’s private key by doing this process backwards. This is called an Elliptic Curve Digital Signature Algorithm.
However, since cryptocurrency is based on this cryptographic function alone, it is not possible to simply change your private key like it is possible to change a password. For this reason, you need to take great care to protect your private key. If your private key is ever compromised, your funds will be at risk.
One of the primary security benefits of a hardware wallet is that it stores your private keys offline. By staying disconnected from the internet, hardware wallets protect your keys from online threats, such as phishing scams or malware. Even if your computer or smartphone is compromised, the private keys stored in your hardware wallet remain safe, as they never interact directly with your online device.
When you initiate a transaction, the transaction details are sent to your hardware wallet, which then securely signs the transaction inside the device using your private key. The private key itself never leaves the hardware wallet, so it remains secure throughout the process. Once the transaction is signed, it’s sent back to your connected device and broadcasted to the network. This ensures your private key is never exposed to the internet, even while conducting transactions.
Why are hardware wallets essential for security?
The main reason many people choose to use a hardware wallet is a concern about the security of funds held on exchanges, especially with recent stories of exchanges collapsing and users losing access to their assets. For this reason, it’s generally recommended not to keep funds on an exchange for extended periods.
With a hardware wallet, you store the keys to your funds, giving you full control over your assets. Unlike an exchange, where control is limited, a hardware wallet ensures that only you have access to your private keys. An added bonus of not holding your funds on an exchange is the lack of withdrawal fees - you’ll only need to pay the necessary transaction fee to send the transaction itself.
A hardware wallet also allows you to store funds across multiple addresses that you control, enhancing your privacy by distributing assets across different addresses.
Types of wallets
When you withdraw funds from an exchange, you transfer them to an address that you control on the blockchain. Beyond withdrawing from your exchange to another exchange, there are two types of wallets you can use for withdrawals:
Hot wallet
A hot wallet is stored on an internet-connected device, such as a mobile app, browser extension, or desktop application (without a hardware wallet). Hot wallets offer convenience and quick access, but because the private key is stored on a device connected to the internet, they are more vulnerable to hacking. Hot wallets are best suited for holding small amounts of funds that you may need frequent access to.
Cold wallet
A cold wallet is a wallet where private keys are generated and stored offline, so they are never exposed to the internet. With a hardware wallet like Trezor, your private key remains offline, providing a high level of security. This makes cold wallets ideal for storing larger amounts of funds or assets you plan to hold for a long period.
Key features to look for in a hardware wallet
Trezor hardware wallets offer robust features to keep your cryptocurrency safe and offline while ensuring convenient access whenever you need it.
Security and PIN protection
A key security feature is PIN protection, which allows you to secure your Trezor with a PIN up to 50 digits long. This provides quick access to your private keys as long as you have the device. If the device is lost, unauthorized access is incredibly unlikely—after each incorrect PIN attempt, the waiting time doubles, and after 16 failed attempts, the device is wiped automatically.
User-friendly design
Trezor devices are designed with ease of use in mind. The Trezor Safe 5 and Trezor Model T offer touchscreens for smooth PIN entry, transaction signing, and wallet recovery. For those who prefer physical buttons, the Trezor Safe 3 and Trezor Model One provide a tactile experience with secure functionality.
Wide cryptocurrency support
Trezor aims to support a broad range of cryptocurrencies from major blockchains. For a detailed list of supported coins and tokens, please refer to our coins page.
Open-source commitment
At Trezor, we believe in transparency through open-source software. Our devices’ code is available for public audit, allowing users to understand exactly how their funds are stored. Trezor has always been, and will always remain, open source.
How to set up and use a hardware wallet
When you buy your first Trezor hardware wallet, you’ll find that setting it up is easier than you might expect. Our Knowledge Base has detailed explanations for each step, but here’s a quick overview of the process:
- Open the box and download Trezor Suite
- Plug in your Trezor device
- Follow the on-screen prompts to create your wallet backup and set your PIN
- Add accounts for the cryptocurrencies you want to use
- You’re all set! You can now send and receive cryptocurrency from your Trezor wallet.
One of the most critical steps is creating your wallet backup. This backup is a list of words that will allow you to restore access to your wallet if something happens to your Trezor device.
Although it may feel like your coins are stored on your Trezor, they are actually held on the blockchain. Your Trezor device simply enables you to access them securely. This also means that your wallet backup provides the same access to your coins as your Trezor device.
If your Trezor device is lost or damaged, your funds can still be recovered with your backup.
However, if someone gains access to your backup, they can access your wallet without needing your Trezor. Keeping your backup secure is essential to protecting your funds.
Ready to move your funds to your Trezor wallet? Follow our step-by-step guide here.
Best practices for hardware wallet security
Now that your Trezor hardware wallet is set up, it’s time to focus on security. With Trezor, you hold the private keys, which means you are the sole owner of your funds. However, if your private keys are lost or compromised, there is no way to recover your funds—Trezor cannot access your wallet backups or help if your device is lost, stolen, or damaged.
Your wallet backup
When setting up your Trezor, you created a wallet backup—a crucial safeguard for your funds. Store this backup securely, and avoid keeping it in the same location as your Trezor device. For added durability, consider using a Trezor Keep Metal, an aerospace-grade steel plate that preserves your backup through floods, fires, and other disasters.
Keep firmware updated
Updating your Trezor firmware is essential for long-term security. However, firmware updates can sometimes wipe the device, so always have your wallet backup accessible in case you need to restore your wallet after an update.
Beware of scams
The cryptocurrency world offers exciting possibilities, but it also attracts scams. Attackers often target users’ wallet backups, employing tactics like phishing emails (sometimes impersonating Trezor) that claim you need to verify your wallet backup online. Remember: Trezor will NEVER ask you to enter your wallet backup digitally (except on your Trezor device if you choose to verify it).
NEVER enter your wallet backup on a computer, phone, or share it with anyone.
Your wallet backup provides unrestricted access to your funds. If you suspect your wallet backup has been compromised, immediately transfer your funds to a new wallet.
How to choose the right hardware wallet for you
Trezor has been protecting digital assets since the launch of the Trezor Model One in 2014.
Our latest generation of hardware wallets offers unmatched security, transparency, and ease of use. They are built for everyone from first-time users to those who demand the highest level of protection.
Trezor Safe 7
Released in 2025, the Trezor Safe 7 is our most advanced wallet yet. It is designed for users who want the strongest security, premium materials, and the most future-ready device.
It features dual (including the open-source chip), Bluetooth connectivity, a 2.5" touchscreen, magnetic wireless charging, and architecture.
If you want the most capable and future-proof hardware wallet available, the Trezor Safe 7 is built for you.
Trezor Safe 5
Released in 2024, the Trezor Safe 5 features a bright color touchscreen and a secure element chip.
Trezor Safe 5 is ideal for users who interact frequently with the blockchain and want a powerful, tactile experience that keeps self-custody simple and secure.
Trezor Safe 3
The Trezor Safe 3, launched in 2023, delivers professional-grade security in a compact form.
It includes a secure element for strong protection and straightforward operation without a touchscreen.
This model is perfect for long-term holders or users who prefer to keep their crypto stored safely offline with minimal interaction.
Frequently Asked Questions (FAQs)
Is a hardware wallet worth it?
If you want peace of mind knowing that you control the keys to your funds, a hardware wallet is absolutely worth it. When funds are kept on an exchange or in a hot wallet, the risk of remote hacks remains. With a hardware wallet and a proper setup, remote access to your funds is impossible (unless you give someone your wallet backup), giving you a much higher level of security.
What is actually stored on a hardware wallet?
A hardware wallet securely stores the private keys to your crypto. It doesn’t store the assets themselves—these remain on the blockchain. In fact, you can use your wallet backup to access your funds on multiple hardware wallets if needed.
At what point should I get a hardware wallet?
Consider a hardware wallet if your crypto holdings are significant enough that an exchange or hot wallet hack would seriously impact you. Trezor enables self-custody, putting control of your assets solely in your hands. While this brings responsibility, with the right education and experience, you’ll become a self-custody pro in no time.
Can hardware wallets be hacked?
Hardware wallets are designed to be highly secure, keeping your private keys offline and protected from online threats.
However, no device is entirely immune to hacking. Here are some key points to consider:
- Physical Security: For a hardware wallet to be compromised, an attacker would typically need physical access to the device, so storing your wallet in a safe place is essential.
- PIN Protection and Backup: Trezor devices are protected by a PIN, and after repeated incorrect attempts, the device is wiped. This makes unauthorized access extremely difficult.
- Firmware Updates: Regularly updating your firmware protects your device from potential vulnerabilities. Trezor’s open-source firmware also benefits from continuous community auditing and security improvements.
While hardware wallets like Trezor offer one of the most secure storage options, the biggest risk often comes from phishing scams or social engineering attacks targeting your wallet backup.
Always keep your wallet backup offline, secure, and never enter it on any digital device.
Final thoughts – why every crypto holder should consider a hardware wallet
Owning a hardware wallet like a Trezor provides peace of mind. With Trezor, your funds are safe from online hacks and each transaction requires physical confirmation on your device—keeping your assets secure as long as your wallet backup is not compromised.
For beginners, starting with a hardware wallet is especially beneficial. Not only does it protect your funds, but it also gives you hands-on experience with blockchain technology. Many new cryptocurrency users leave their assets on an exchange, missing out on the understanding of how it works and why it’s valuable. Using a hardware wallet teaches you about wallet backups, private keys, and on-chain transactions, empowering you with knowledge that will deepen your understanding of cryptocurrency and self-custody.
Ready to take control of your crypto assets? Visit our e-shop to begin your journey toward secure self-custody today!