Safe & secure Viper Cash wallet
Take control of your Viper Cash assets with complete confidence in the Trezor ecosystem.
- Secured by your hardware wallet
- Use with compatible hot wallets
- Trusted by over 2 million customers
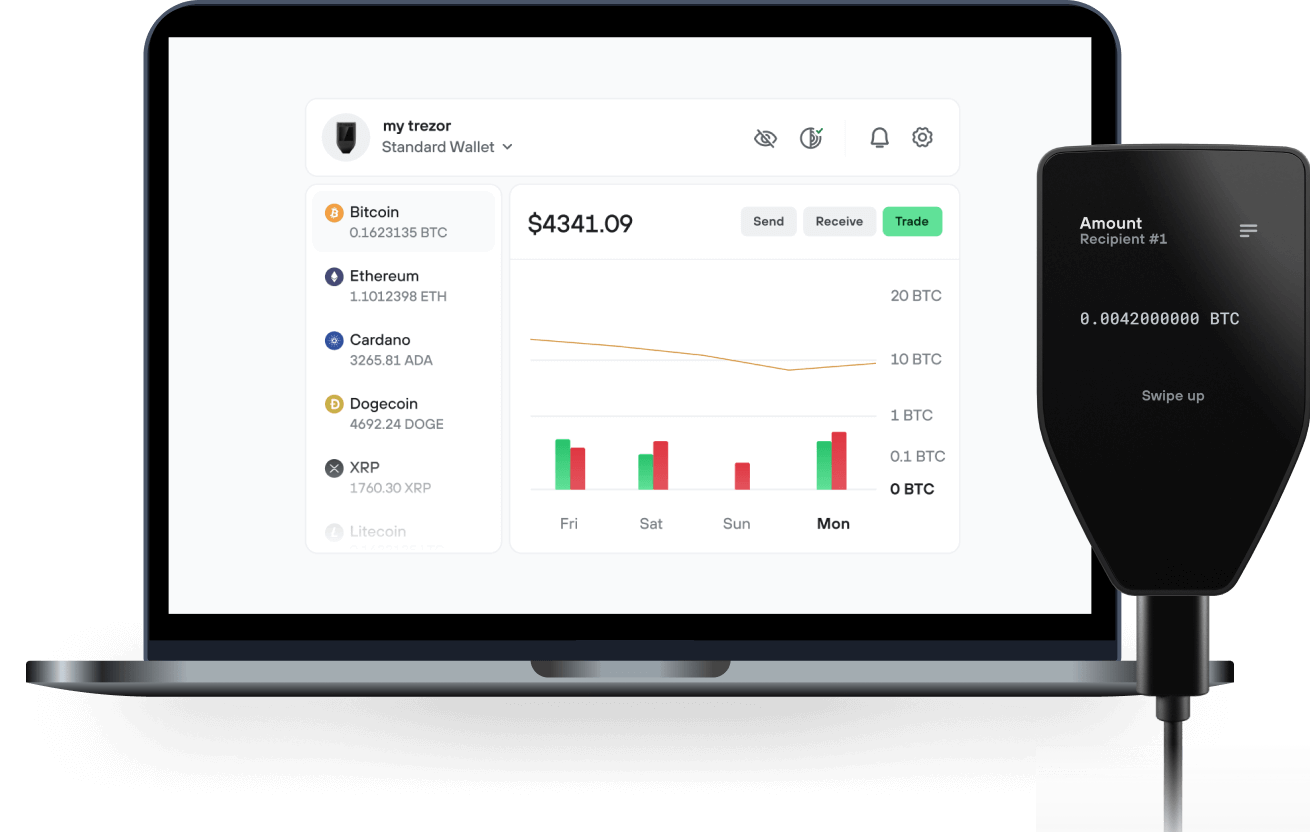
Send & receive your Viper Cash with the Trezor Suite app

Send & receive
Trezor hardware wallets that support Viper Cash
Sync your Trezor with wallet apps
Manage your Viper Cash with your Trezor hardware wallet synced with several wallet apps.
Trezor Suite
MetaMask
Rabby
Supported Viper Cash Network
- Ethereum
Why a hardware wallet?
Go offline with Trezor
- You own 100% of your coins
- Your wallet is 100% safe offline
- Your data is 100% anonymous
- Your coins aren’t tied to any company
Online exchanges
- If an exchange fails, you lose your coins
- Exchanges are targets for hackers
- Your personal data may be exposed
- You don’t truly own your coins
How to VIP on Trezor
Connect your Trezor
Open a third-party wallet app
Manage your assets
Make the most of your VIP
Trezor keeps your VIP secure
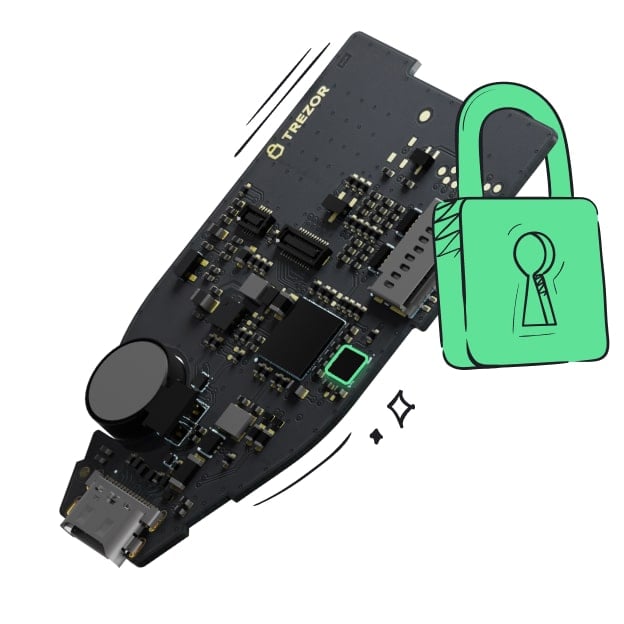 Protected by Secure Element
Protected by Secure ElementThe best defense against both online and offline threats
 Your tokens, your control
Your tokens, your controlAbsolute control of every transaction with on-device confirmation
 Security starts with open-source
Security starts with open-sourceTransparent wallet design makes your Trezor better and safer
 Clear & simple wallet backup
Clear & simple wallet backupRecover access to your digital assets with a new backup standard
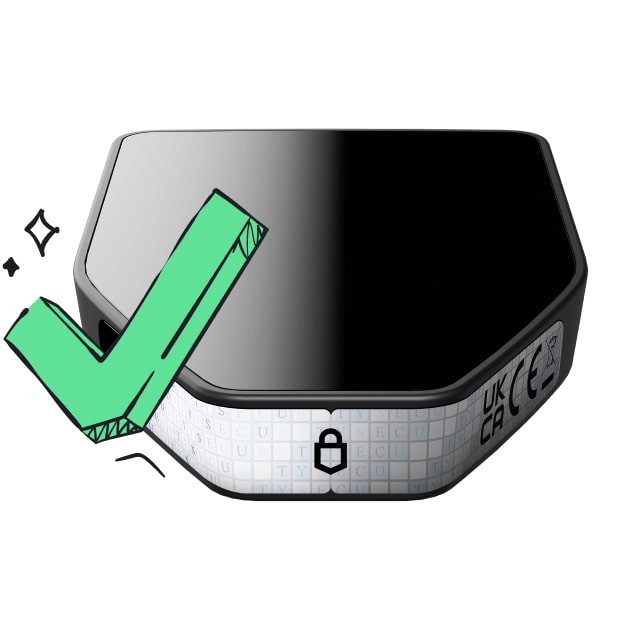 Confidence from day one
Confidence from day onePackaging & device security seals protect your Trezor’s integrity
VIPER CASH is a censorship-resistant bridge that connects Zcash-grade privacy to any chain.
Instead of broadcasting transactions to public mempools, users sign encrypted intents (e.g., swap USDC on Base → receive SOL on Solana). Off-chain solvers compete to provide the best all-in execution price, and settlement occurs through RAILGUN shielded pools and Relay cross-chain proofs with no linkable addresses, no orderflow leakage, and no centralized custodians.
The native token, VIP, powers the network by enabling gasless transfers, fee rebates, and relayer/solver participation, ensuring privacy, neutrality, and censorship-resistance by design.