Safe & secure Moonwell wallet
Take control of your Moonwell assets with complete confidence in the Trezor ecosystem.
- Secured by your hardware wallet
- Use with compatible hot wallets
- Trusted by over 2 million customers
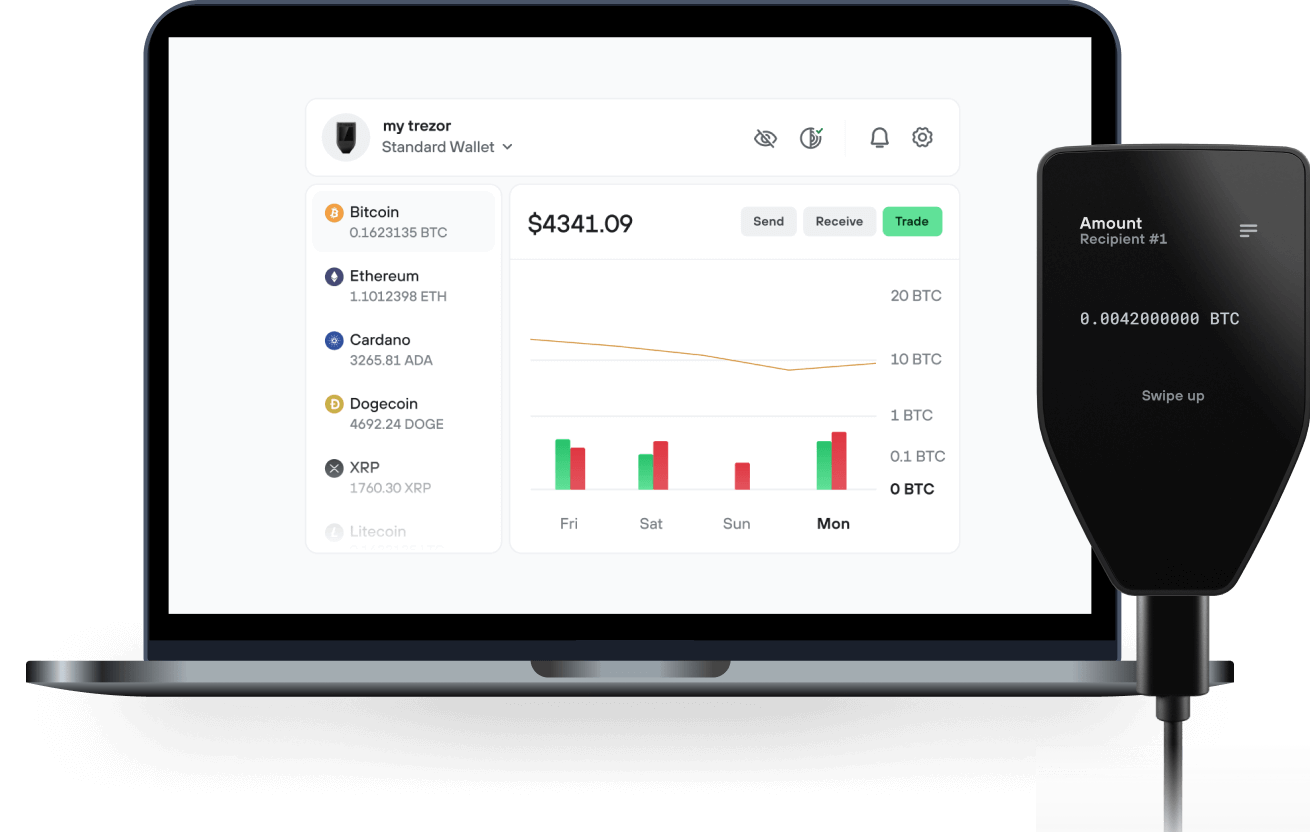
Send & receive your Moonwell with the Trezor Suite app

Send & receive
Trezor hardware wallets that support Moonwell
Sync your Trezor with wallet apps
Manage your Moonwell with your Trezor hardware wallet synced with several wallet apps.
Trezor Suite
MetaMask
Rabby
Supported Moonwell Networks
- Base
- Moonbeam
Why a hardware wallet?
Go offline with Trezor
- You own 100% of your coins
- Your wallet is 100% safe offline
- Your data is 100% anonymous
- Your coins aren’t tied to any company
Online exchanges
- If an exchange fails, you lose your coins
- Exchanges are targets for hackers
- Your personal data may be exposed
- You don’t truly own your coins
How to WELL on Trezor
Connect your Trezor
Open a third-party wallet app
Manage your assets
Make the most of your WELL
Trezor keeps your WELL secure
 Protected by Secure Element
Protected by Secure ElementThe best defense against both online and offline threats
 Your tokens, your control
Your tokens, your controlAbsolute control of every transaction with on-device confirmation
 Security starts with open-source
Security starts with open-sourceTransparent wallet design makes your Trezor better and safer
 Clear & simple wallet backup
Clear & simple wallet backupRecover access to your digital assets with a new backup standard
 Confidence from day one
Confidence from day onePackaging & device security seals protect your Trezor’s integrity
Moonwell Artemis uses battle tested code from the Moonwell Apollo protocol to provide an open, non-custodial lending and borrowing DeFi protocol. While Apollo is a community driven protocol with innovative features, Artemis users will enjoy polished features with faster transaction times, while still preserving the same level of security.
Moonwell’s goal is to be the most user-friendly, fast, and secure DeFi protocol in the ecosystem. With this in mind, an emphasis was placed on having a high standard of security. Multi-signature systems are implemented for all smart contracts used by the protocol, with the expert cyber-security team at Halborn Security auditing all contracts before deployment. Additionally, there is a generous bounty program through a partnership with the trusted team at ImmuneFi, which allows security researchers to submit their findings for review and earn a bounty for discovering security vulnerabilities.