Safe & secure Jackal Protocol wallet
Take control of your Jackal Protocol assets with complete confidence in the Trezor ecosystem.
- Secured by your hardware wallet
- Use with compatible hot wallets
- Trusted by over 2 million customers
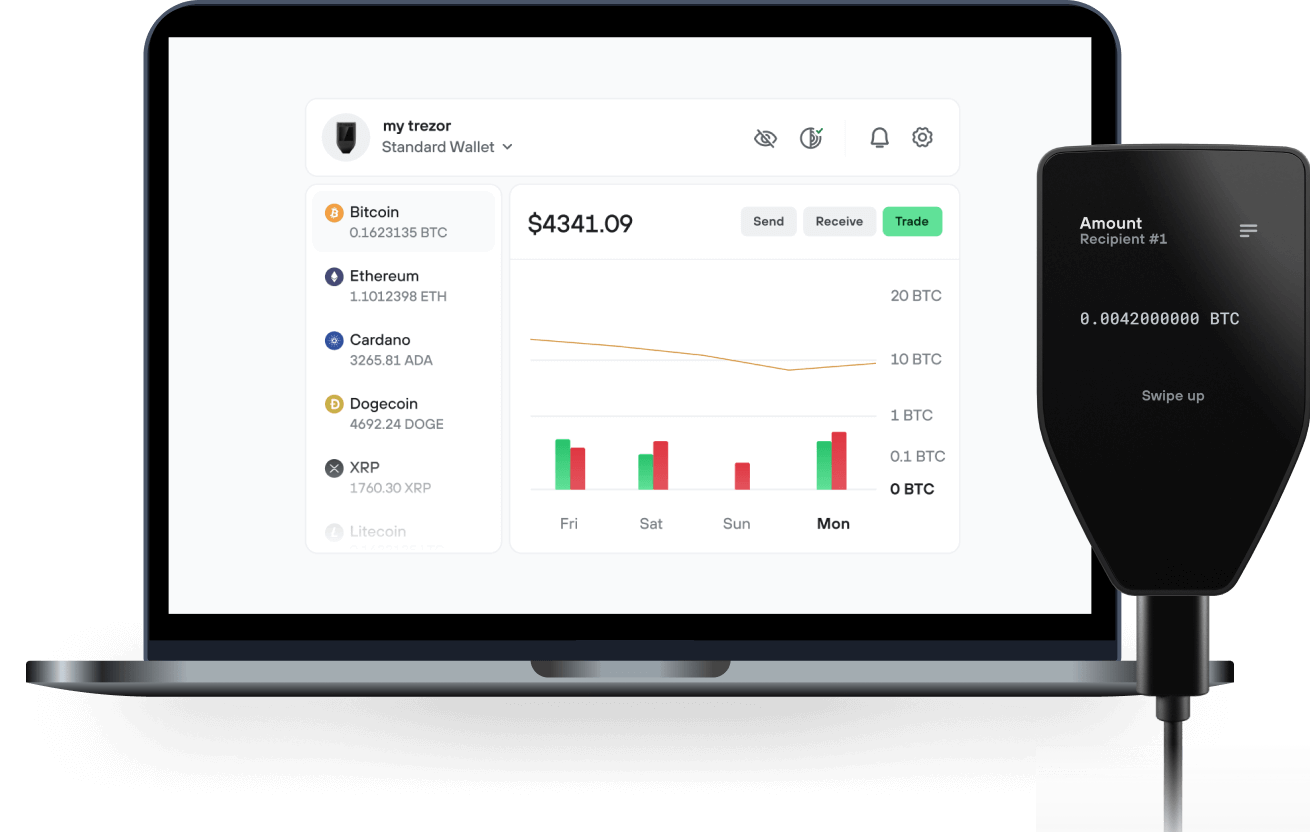
Send & receive your Jackal Protocol with the Trezor Suite app

Send & receive
Trezor hardware wallets that support Jackal Protocol
Sync your Trezor with wallet apps
Manage your Jackal Protocol with your Trezor hardware wallet synced with several wallet apps.
Trezor Suite
MetaMask
Rabby
Supported Jackal Protocol Network
- Base
Why a hardware wallet?
Go offline with Trezor
- You own 100% of your coins
- Your wallet is 100% safe offline
- Your data is 100% anonymous
- Your coins aren’t tied to any company
Online exchanges
- If an exchange fails, you lose your coins
- Exchanges are targets for hackers
- Your personal data may be exposed
- You don’t truly own your coins
How to JKL on Trezor
Connect your Trezor
Open a third-party wallet app
Manage your assets
Make the most of your JKL
Trezor keeps your JKL secure
 Protected by Secure Element
Protected by Secure ElementThe best defense against both online and offline threats
 Your tokens, your control
Your tokens, your controlAbsolute control of every transaction with on-device confirmation
 Security starts with open-source
Security starts with open-sourceTransparent wallet design makes your Trezor better and safer
 Clear & simple wallet backup
Clear & simple wallet backupRecover access to your digital assets with a new backup standard
 Confidence from day one
Confidence from day onePackaging & device security seals protect your Trezor’s integrity
Jackal Protocol is a blockchain and data storage network that is fast, ultra-secure, and easy for people to use. The Jackal Protocol is a Cosmos layer 1 blockchain.
The Jackal Protocol allows developers to build decentralized applications with the ability to interface with all Jackal Protocol Modules-including storage contracts and file structure. This grants developers the ability to adjust the ownership of data, share data with other jackal users or smart contracts, and transfer small or large amounts of encrypted data without centralized storage providers or middleware. Data on the Protocol is always self-custodial, meaning no one- not even the team at Jackal-can access or view user data.

