Safe & secure Cap USD wallet
Take control of your Cap USD assets with complete confidence in the Trezor ecosystem.
- Secured by your hardware wallet
- Use with compatible hot wallets
- Trusted by over 2 million customers
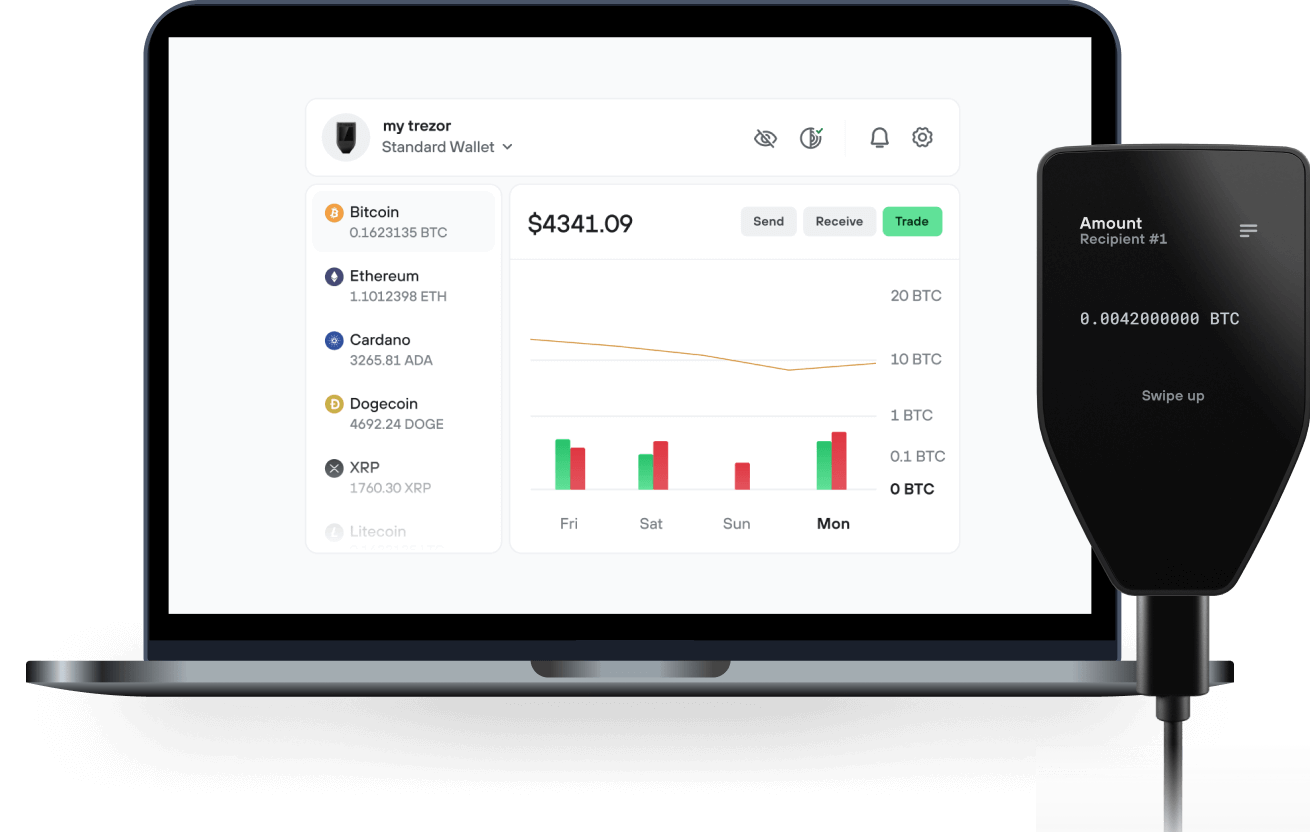
Send & receive your Cap USD with the Trezor Suite app

Send & receive

Swap
Trezor hardware wallets that support Cap USD
Sync your Trezor with wallet apps
Manage your Cap USD with your Trezor hardware wallet synced with several wallet apps.
Trezor Suite
MetaMask
Rabby
Supported Cap USD Network
- Ethereum
Why a hardware wallet?
Go offline with Trezor
- You own 100% of your coins
- Your wallet is 100% safe offline
- Your data is 100% anonymous
- Your coins aren’t tied to any company
Online exchanges
- If an exchange fails, you lose your coins
- Exchanges are targets for hackers
- Your personal data may be exposed
- You don’t truly own your coins
How to CUSD on Trezor
Connect your Trezor
Install Trezor Suite app
Transfer your CUSD
Make the most of your CUSD
Trezor keeps your CUSD secure
 Protected by Secure Element
Protected by Secure ElementThe best defense against both online and offline threats
 Your tokens, your control
Your tokens, your controlAbsolute control of every transaction with on-device confirmation
 Security starts with open-source
Security starts with open-sourceTransparent wallet design makes your Trezor better and safer
 Clear & simple wallet backup
Clear & simple wallet backupRecover access to your digital assets with a new backup standard
 Confidence from day one
Confidence from day onePackaging & device security seals protect your Trezor’s integrity
Cap is a stablecoin protocol that provides credible financial guarantees via two products: the dollar-denominated cUSD and the yield-bearing stcUSD.
cUSD is a digital dollar issued on the Ethereum blockchain that can be used on any network. cUSD's reserve is backed by blue chip stablecoins such as USDC, USDT, pyUSD, BUIDL, and BENJI, i.e. issued by regulated institutions with transparent attestations. It is 1:1 redeemable for any of the available reserve assets.
stcUSD is a savings product issued by staking cUSD. Any cUSD holder has open access to stcUSD. Yield is generated via an autonomous layer of operators, who self-select in and out based on the current hurdle rate of the protocol. The risk of yield generation is covered, meaning users have full downside protection that is verifiable by code.

