Trezor firmware revision check
Firmware authenticity check
The firmware authenticity check is designed to be an extra safeguard against counterfeit Trezor devices. Such devices appear sporadically, primarily on unauthorized e-shops or marketplaces. This additional device authenticity check helps catch more advanced fake devices in circulation.
How does the firmware authenticity check work?
Each firmware binary has several properties, including:
- Firmware version
- RevisionID attribute
These properties are stored in Trezor Suite, as well as on a remote server (data repository), which means we have records of all released firmware versions and their revisions.
Your Trezor device communicates these features with the Suite application, which then checks them against the stored database.
- If these attributes match, nothing happens, and you can continue using Trezor Suite as usual.
- If they do not match, Suite will display the following warning modal:
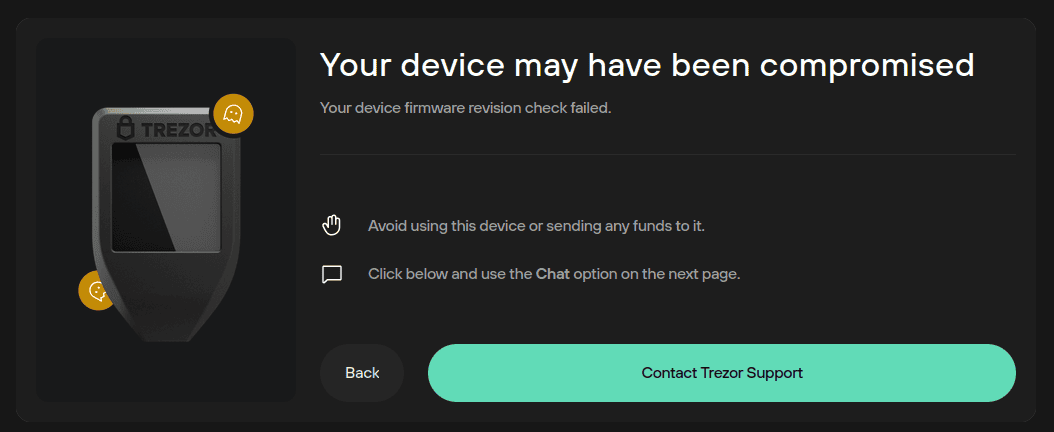
Access to Trezor Suite is effectively blocked at this stage, and you must click the Contact Trezor Support button to resolve your issue.
As the database is stored in the Trezor Suite app, these checks occur even if Suite is offline, but there are several different scenarios for the firmware check:
Scenario 1: Trezor Suite is online and the device firmware version present in the local database
- Firmware version and RevisionID on the Trezor device match those stored in the Trezor Suite database: OK
- Firmware version and RevisionID on the device do not match those stored in the Trezor Suite database: Suite is blocked, and the warning modal is shown.
Scenario 2: Trezor Suite is online and the device firmware version present in the local database
- Trezor Suite looks for the remote database in the Data repository and checks it; firmware version and RevisionID on the device match those stored in the Trezor Suite database: OK
- Trezor Suite looks for the remote database in the Data repository and checks it; firmware version and RevisionID on the device do not match those stored in the Trezor Suite database: Suite is blocked, and the warning modal is shown.
Scenario 3: Trezor Suite is offline and the device firmware version present in the local database
- Trezor Suite checks and the firmware version and RevisionID on the device match those stored in the Trezor Suite database: OK
- Trezor Suite checks and the firmware version and RevisionID on the device do not match those stored in the Trezor Suite database: Suite is blocked, and the warning modal is shown.
Scenario 4: Trezor Suite is offline and the device firmware version present in the local database
- Trezor Suite checks the local database, and the firmware version is not stored there; the remote database cannot be downloaded (Suite is offline), so Suite displays this banner at the top of the screen:
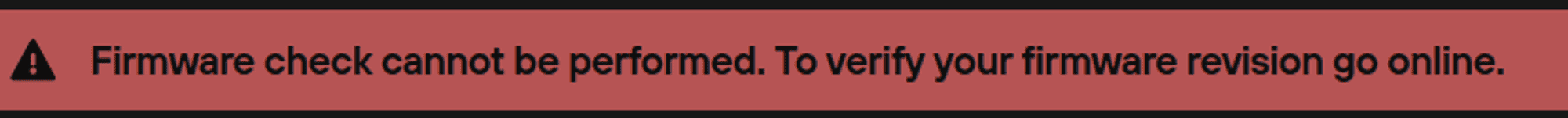
- Once online, the banner disappears; Suite looks for the remote database in the Data repository, checks it, and if the firmware version and RevisionID on the device match those stored in the Trezor Suite database: OK
- Trezor Suite looks for the remote database in the Data repository, checks it, and if the firmware version and RevisionID on the device do not match those stored in the Trezor Suite database: Suite is blocked, and the warning modal is shown.
Disabling firmware authenticity check
The firmware authenticity check can be turned on/off via Settings > Device > Danger area:
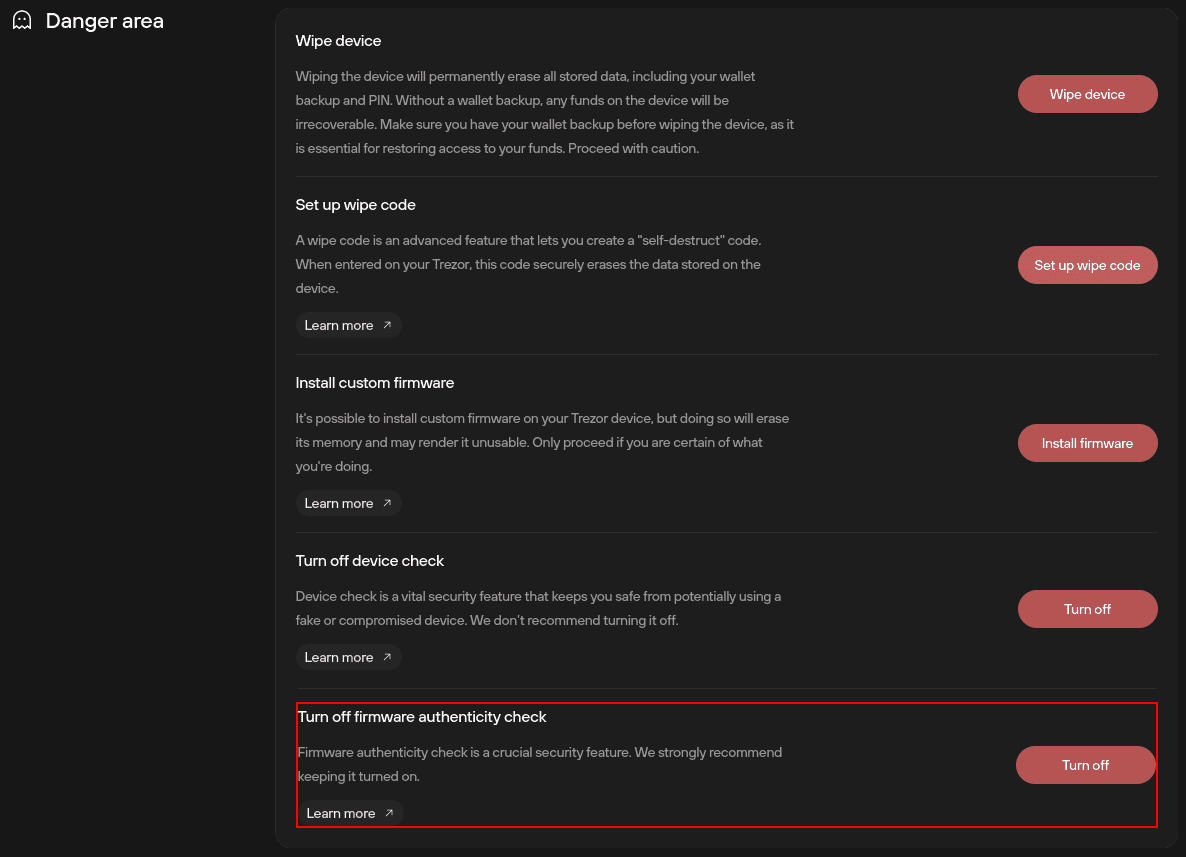
These security checks should only be disabled for testing and development purposes (with firmware that has not yet been released).