Safe & secure QLix wallet
Take control of your QLix assets with complete confidence in the Trezor ecosystem.
- Secured by your hardware wallet
- Use with compatible hot wallets
- Trusted by over 2 million customers
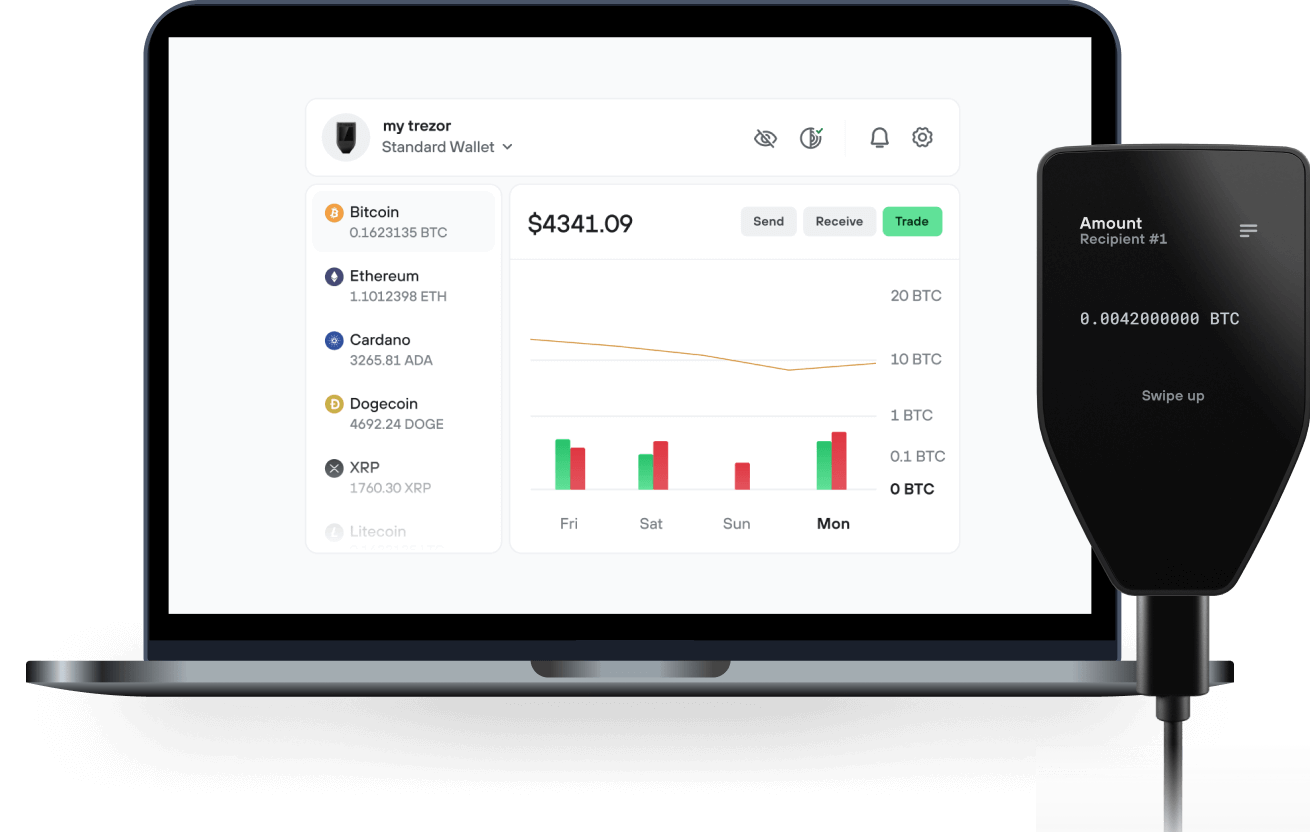
Send & receive your QLix with the Trezor Suite app

Send & receive
Trezor hardware wallets that support QLix
Sync your Trezor with wallet apps
Manage your QLix with your Trezor hardware wallet synced with several wallet apps.
Trezor Suite
MetaMask
Rabby
Supported QLix Network
- Ethereum
Why a hardware wallet?
Go offline with Trezor
- You own 100% of your coins
- Your wallet is 100% safe offline
- Your data is 100% anonymous
- Your coins aren’t tied to any company
Online exchanges
- If an exchange fails, you lose your coins
- Exchanges are targets for hackers
- Your personal data may be exposed
- You don’t truly own your coins
How to QLIX on Trezor
Connect your Trezor
Open a third-party wallet app
Manage your assets
Make the most of your QLIX
Trezor keeps your QLIX secure
 Protected by Secure Element
Protected by Secure ElementThe best defense against both online and offline threats
 Your tokens, your control
Your tokens, your controlAbsolute control of every transaction with on-device confirmation
 Security starts with open-source
Security starts with open-sourceTransparent wallet design makes your Trezor better and safer
 Clear & simple wallet backup
Clear & simple wallet backupRecover access to your digital assets with a new backup standard
 Confidence from day one
Confidence from day onePackaging & device security seals protect your Trezor’s integrity
QLix stands as a pioneering cryptocurrency project, introducing a novel approach called Quantitative Liquidity Mixing. It functions as both a bridge and a mixer, optimizing liquidity provision across blockchain networks while ensuring transaction privacy. Utilizing advanced quantitative analysis, smart routing algorithms, and privacy-preserving techniques, QLix facilitates efficient and confidential asset transfers, enhancing the interoperability and fungibility of digital assets. QLix employs state-of-the-art cryptographic methods, including zero-knowledge proofs and other privacy-preserving protocols, to anonymize transactions. These techniques obfuscate the origins and destinations of digital assets, allowing users to enjoy a high level of privacy and security in their transactions, making the movement of assets across blockchains trace-resistant.