Safe & secure KAGE NETWORK wallet
Take control of your KAGE NETWORK assets with complete confidence in the Trezor ecosystem.
- Secured by your hardware wallet
- Use with compatible hot wallets
- Trusted by over 2 million customers
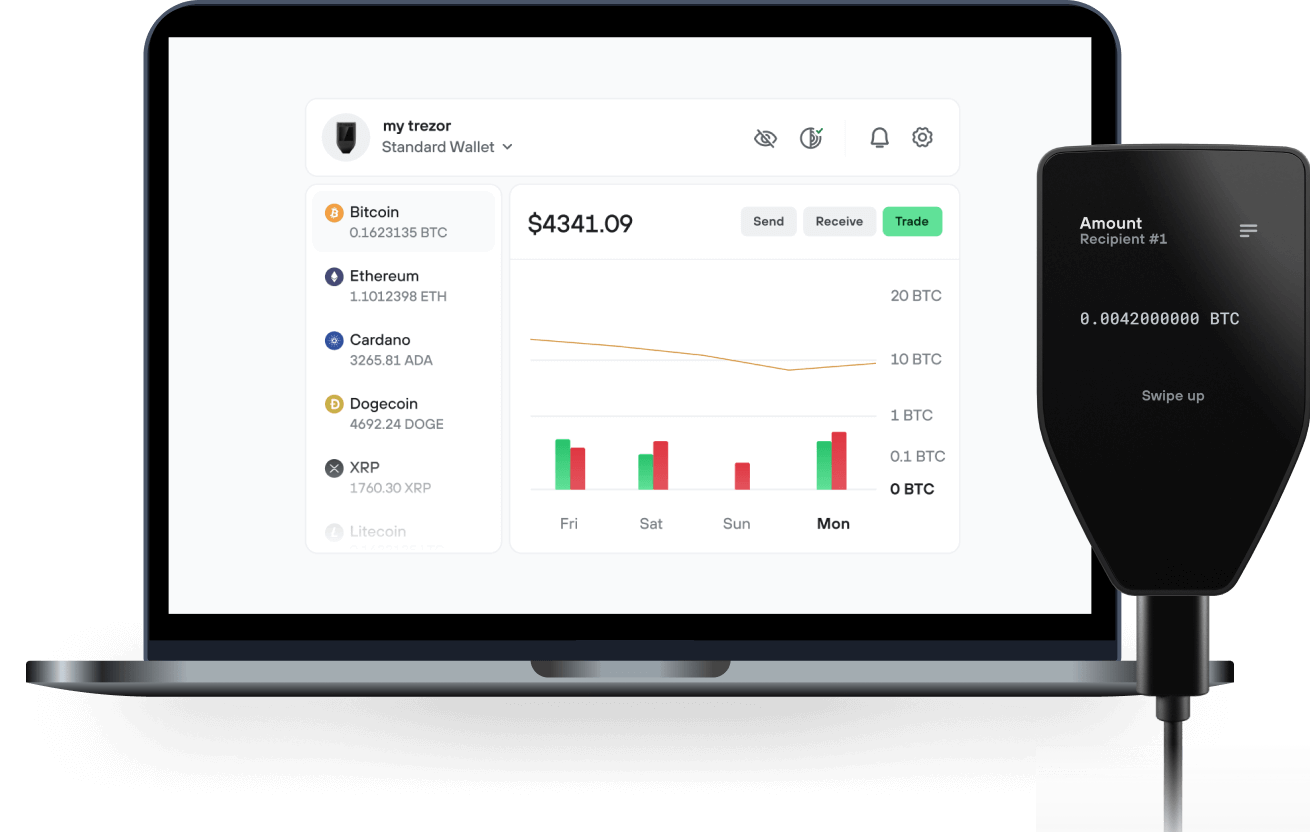
Send & receive your KAGE NETWORK with the Trezor Suite app

Send & receive
Trezor hardware wallets that support KAGE NETWORK
Sync your Trezor with wallet apps
Manage your KAGE NETWORK with your Trezor hardware wallet synced with several wallet apps.
Trezor Suite
MetaMask
Rabby
Supported KAGE NETWORK Network
- Ethereum
Why a hardware wallet?
Go offline with Trezor
- You own 100% of your coins
- Your wallet is 100% safe offline
- Your data is 100% anonymous
- Your coins aren’t tied to any company
Online exchanges
- If an exchange fails, you lose your coins
- Exchanges are targets for hackers
- Your personal data may be exposed
- You don’t truly own your coins
How to KAGE on Trezor
Connect your Trezor
Open a third-party wallet app
Manage your assets
Make the most of your KAGE
Trezor keeps your KAGE secure
 Protected by Secure Element
Protected by Secure ElementThe best defense against both online and offline threats
 Your tokens, your control
Your tokens, your controlAbsolute control of every transaction with on-device confirmation
 Security starts with open-source
Security starts with open-sourceTransparent wallet design makes your Trezor better and safer
 Clear & simple wallet backup
Clear & simple wallet backupRecover access to your digital assets with a new backup standard
 Confidence from day one
Confidence from day onePackaging & device security seals protect your Trezor’s integrity
Building The Hardware Layer Of The Privacy-Focused Online Economy With A Battle-Tested Decentralized VPN Router Solution
With the unprecedented scale of digital data collection, increasingly sophisticated cyber threats, and ever-present government overreach, online privacy has never been more important. The proliferation of smart devices, IoT infrastructure and AI software is only set to amplify online risks by creating numerous new entry points for potential breaches. This has led to skyrocketing demand for privacy solutions, with the privacy-enhancing technology market forecast to exceed $24b by 2024.
VPNs (Virtual Private Networks) have emerged as a leading solution for online privacy due to their ability to encrypt internet traffic and mask users' IP addresses, effectively shielding personal data from prying eyes. This makes VPNs a reliable method for maintaining anonymity and protecting sensitive information. Indeed, adoption of VPNs has become so widespread that a recent Forbes report found that 33% of internet users worldwide have a VPN.
However, the current generation of centralized, software-based VPNs are replete with vulnerabilities and inefficiencies that limit their effectiveness as a long-term solution for delivering online security and privacy at scale. Software-based VPNs were designed with a single device - usually a personal computer - in mind. They struggle to handle the multi-device connected homes that users now find themselves in, which can include connected TVs, fridges, cameras and an ever growing list of IoT devices. Meanwhile, whilst early adopters were comfortable working with abstract software, mainstream consumers are seeking a simpler, plug and play solution. In addition to this, centralized VPN business models concentrate control and access to vast amounts of sensitive user data in the hands of a single entity. This creates a single point of failure and also opens up the possibility of governments compelling them to share data.